Dmitry Sokolov recommends UnHackMe!
UnHackMe is a powerful tool against malware.
UnHackMe quickly removes rootkits/malware/adware/browser hijack issues!
 (5 / 5)
(5 / 5)
Worm.Allaple-213 also known as W32.CrypticB.Trojan, Trojan.Win32.Allaple.bkbmt, Worm.Allaple.Gen.
Malware Analysis of Worm.Allaple-213 – HJESKHBE.EXE
Created files:
%Local Appdata%\Google\Chrome\User Data\Default\Extensions\felcaaldnbdncclmgdcncolpebgiejap\1.0_0\tlblhqjn.exe
%Local Appdata%\Google\Chrome\User Data\Default\Extensions\nmmhkkegccagdldgiimedpiccmgmieda\0.0.6.1_0\html\tlblhqjn.exe
%Program Files Common%\Microsoft Shared\Smart Tag\1049\hjeskhbe.exe
%Program Files Common%\Microsoft Shared\Stationery\bcwvzwbh.exe
%Program Files Common%\Microsoft Shared\Stationery\bhrhnkht.exe
Autostart registry keys:
HKLM\Software\Classes\CLSID\{0BD9D438-2B62-1078-724B-E27EBD7F7A8F}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\czjevcet.exe”
HKLM\Software\Classes\CLSID\{347B1259-E23B-97AA-90DE-1F87B6B38A33}\LocalServer32\: “%Local Appdata%\Google\Chrome\User Data\Default\Extensions\nmmhkkegccagdldgiimedpiccmgmieda\0.0.6.1_0\html\tlblhqjn.exe”
HKLM\Software\Classes\CLSID\{35349B95-82D3-1178-19ED-0E5D2312F5C0}\LocalServer32\: “%SysDir%\urdvxc.exe”
HKLM\Software\Classes\CLSID\{41B2340A-2DC9-B06E-C6F2-D09099C23FA8}\LocalServer32\: “%Desktop%\Warrior\zhlqjlwk.exe”
HKLM\Software\Classes\CLSID\{4222E084-9879-6354-96E0-20C15ACDC125}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\qjllsjhl.exe”
HKLM\Software\Classes\CLSID\{4C80FDD5-398A-C978-C78B-16A1293DD4DE}\LocalServer32\: “%Program Files Common%\System\ado\tsektjkj.exe”
HKLM\Software\Classes\CLSID\{541C14FC-A3AA-C18E-DBF1-600A7FA7940B}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\bhrhnkht.exe”
HKLM\Software\Classes\CLSID\{57B24AA4-B776-3CB3-3A11-725E7736C158}\LocalServer32\: “%Appdata%\Auslogics\Disk Defrag\Reports\tvxshctj.exe”
HKLM\Software\Classes\CLSID\{6455A07B-5629-2D89-9412-B3A2DD705BDE}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\bcwvzwbh.exe”
HKLM\Software\Classes\CLSID\{68A7BB51-0E11-8E6A-8D94-E21986612658}\LocalServer32\: “c:\sand-box\3f71a27b88d47630943c8d8a5632b729.exe”
HKLM\Software\Classes\CLSID\{76126225-3758-4FE5-19E1-0942B74619EF}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\bnbtzwxt.exe”
HKLM\Software\Classes\CLSID\{7D2E936C-285C-5A66-3FE8-B76B480783C6}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\xrljqjzn.exe”
HKLM\Software\Classes\CLSID\{83B5D292-A22F-1B4A-D7F2-07B54755FFF0}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\bzqlkhrh.exe”
HKLM\Software\Classes\CLSID\{983CB576-F105-8BC6-0DB8-F2C0DD84BEED}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\ehbebsrn.exe”
HKLM\Software\Classes\CLSID\{9B995423-493C-874A-B498-AF856BE7A7B2}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\tlcwjrwt.exe”
HKLM\Software\Classes\CLSID\{A18CE63E-6C47-00A5-8688-927B7EB5E2B5}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\nsqjttkv.exe”
HKLM\Software\Classes\CLSID\{A572761A-8C09-6F81-8A7D-33A5FEE989B9}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\elwtjnbj.exe”
HKLM\Software\Classes\CLSID\{B7536FB0-4169-89A0-FC6E-26BB21D3DF7C}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Smart Tag\1049\hjeskhbe.exe”
HKLM\Software\Classes\CLSID\{CC796051-4B90-8169-4C3B-CB00CBC2A1E0}\LocalServer32\: “%Program Files%\Microsoft Office\OFFICE11\1049\bztzcwss.exe”
HKLM\Software\Classes\CLSID\{CFC77ED3-B1EB-647F-0F41-2AE1496A3AAC}\LocalServer32\: “%Program Files%\Microsoft Office\OFFICE11\1049\znerrjbc.exe”
HKLM\Software\Classes\CLSID\{D2498B94-25F7-A0BB-F8CD-F0F9FF4DFDC3}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\vkjljzrn.exe”
HKLM\Software\Classes\CLSID\{D4A634E8-D378-EE77-8A7A-7FF9B86EFC55}\LocalServer32\: “%Program Files%\Microsoft Office\OFFICE11\rsrrhtck.exe”
HKLM\Software\Classes\CLSID\{E59D9298-124D-2169-BC13-EA9ED9A48DC0}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\njbsvtll.exe”
HKLM\Software\Classes\CLSID\{F3D1F763-6168-A4AA-AE26-04F83B3404B0}\LocalServer32\: “%Program Files Common%\Microsoft Shared\Stationery\brvrjrke.exe”
HKLM\System\CurrentControlSet\Services\MSWindows\ImagePath: “”%SysDir%\urdvxc.exe” /service”
HKLM\System\CurrentControlSet\Services\MSWindows\DisplayName: “Network Windows Service”
Detected by UnHackMe:
HJESKHBE.EXE
Default location: %PROGRAM FILES COMMON%\MICROSOFT SHARED\SMART TAG\1049\HJESKHBE.EXE
Dropper hash(md5): 3f71a27b88d47630943c8d8a5632b729
UnHackMe
removes malware invisible for your antivirus!
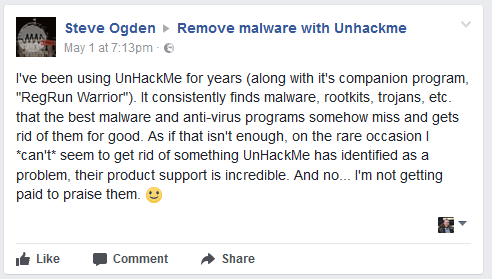
UnHackMe is 100% CLEAN, which means it does not contain any form of malware, including adware, spyware, viruses, trojans and backdoors. VirusTotal (0/56).
System Requirements: Windows 2000-Windows 8.1/10. UnHackMe uses minimum of computer resources.